You probably already know that a User Account in Active Directory is an Active Directory Object, or simply said, a record in an AD database. Most of the time we create user accounts for people, however user accounts can also be created for applications or processes.
User accounts allow a person to access resources on a network. But we can just as easily deny access to certain resources on the network through the user account. That’s why, User Account Objects are quite important and very useful.
Today I’ll show you how easy it is to create a new user account, create a user template and how to use a template in Server 2008 Active Directory. Next week we’ll discuss User Groups and Organizational Units. Now, let’s get started with creating a user account.
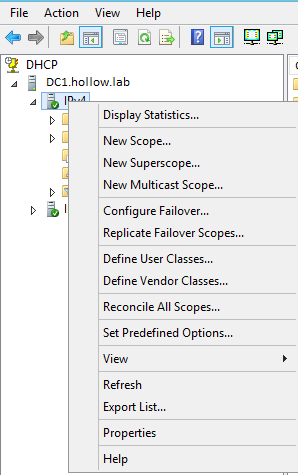
2. Next we will open up the Roles section, next to Active Directory Users and Computers section and finally the Active Directory Users and Computers. You should now see your domain name.
3. We are going to click on our Users section where we are going to create a new User Account. To do so, right-click on the blank section, point to New and select User.
4. In this window you need to type in the user’s first name, middle initial and last name. Next you will need to create a user’s logon name.
In our example we are going to create a user account for Billy Miles and his logon name will be bmiles. When done, click on the Next button.
5. In the next window you will need to create a password for your new user and select appropriate options.
In our example we are going to have the user change his password at his next logon. You can also prevent a user from changing his password, set the password so that it will never expire or completely disable the account.
When you are done making your selections, click the Next button.
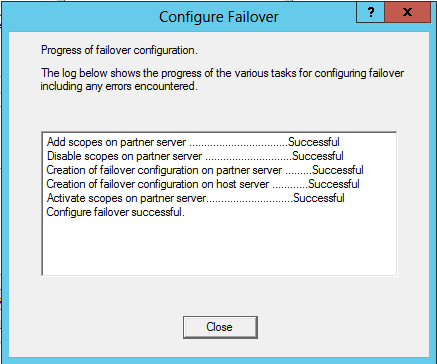
6. And finally, click on the Finish button to complete the creation of new User Account.
You may have multiple user templates for multiple purposes with different settings and properties. There is no limit on the number of user templates, but keep in mind that they are there to help you, not to confuse you, so keep in mind less is better.
To create a user template, we are going to create a regular user account just like we did above. A little note here, you may want to add an * as the first character of the name so it floats at the top in AD and is much easier to find.
1. To start out, right-click on the empty space, point to new, and select User.
2. Type in the user’s name (with asterisks if so desired) and click Next.
3. Create the template’s password and do not forget to check the box next to the Account is disabled option. When ready, click Next.
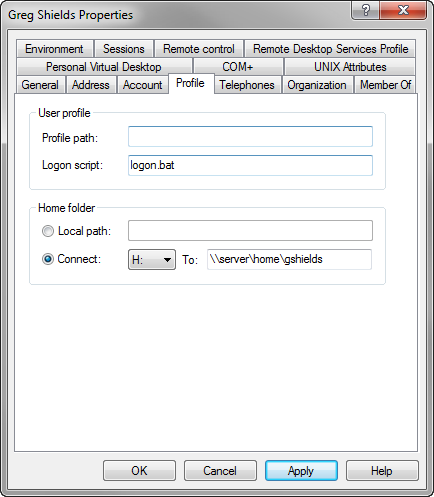
4. Once the account is created, you can go ahead and add all the properties you need for that template. To do so, double-click on that account and navigate to a specific tab. Once done click OK.
We can do that for as many users as needed. Let’s start by right-clicking on the template and selecting Copy.
2. Next we are going to enter the user’s name, login and password information while making sure the checkbox next to Account is disabled is unchecked.
3. Once we finish, our new user account is created with all the properties of the template account. Now wasn’t that easy!
User accounts allow a person to access resources on a network. But we can just as easily deny access to certain resources on the network through the user account. That’s why, User Account Objects are quite important and very useful.
Today I’ll show you how easy it is to create a new user account, create a user template and how to use a template in Server 2008 Active Directory. Next week we’ll discuss User Groups and Organizational Units. Now, let’s get started with creating a user account.
How To Create a New User Account in Active Directory
1. To start let’s go ahead and open up Server Manager2. Next we will open up the Roles section, next to Active Directory Users and Computers section and finally the Active Directory Users and Computers. You should now see your domain name.
3. We are going to click on our Users section where we are going to create a new User Account. To do so, right-click on the blank section, point to New and select User.
4. In this window you need to type in the user’s first name, middle initial and last name. Next you will need to create a user’s logon name.
In our example we are going to create a user account for Billy Miles and his logon name will be bmiles. When done, click on the Next button.
5. In the next window you will need to create a password for your new user and select appropriate options.
In our example we are going to have the user change his password at his next logon. You can also prevent a user from changing his password, set the password so that it will never expire or completely disable the account.
When you are done making your selections, click the Next button.
6. And finally, click on the Finish button to complete the creation of new User Account.
How To Create a User Template in Active Directory
A user template in Active Directory will make your life a little easier, especially if you are creating users for a specific department, with exactly the same properties, and membership to the same user groups. A user template is nothing more than a disabled user account that has all these settings already in place. The only thing you are doing is copying this account, adding a new name and a password.You may have multiple user templates for multiple purposes with different settings and properties. There is no limit on the number of user templates, but keep in mind that they are there to help you, not to confuse you, so keep in mind less is better.
To create a user template, we are going to create a regular user account just like we did above. A little note here, you may want to add an * as the first character of the name so it floats at the top in AD and is much easier to find.
1. To start out, right-click on the empty space, point to new, and select User.
2. Type in the user’s name (with asterisks if so desired) and click Next.
3. Create the template’s password and do not forget to check the box next to the Account is disabled option. When ready, click Next.
4. Once the account is created, you can go ahead and add all the properties you need for that template. To do so, double-click on that account and navigate to a specific tab. Once done click OK.
How To Use a User Template in Active Directory
1. Now in order to use that user template, we are going to select it, copy it and add the unique information such as user name, password, etc.We can do that for as many users as needed. Let’s start by right-clicking on the template and selecting Copy.
2. Next we are going to enter the user’s name, login and password information while making sure the checkbox next to Account is disabled is unchecked.
3. Once we finish, our new user account is created with all the properties of the template account. Now wasn’t that easy!


 8:55 PM
8:55 PM














 Posted in:
Posted in: